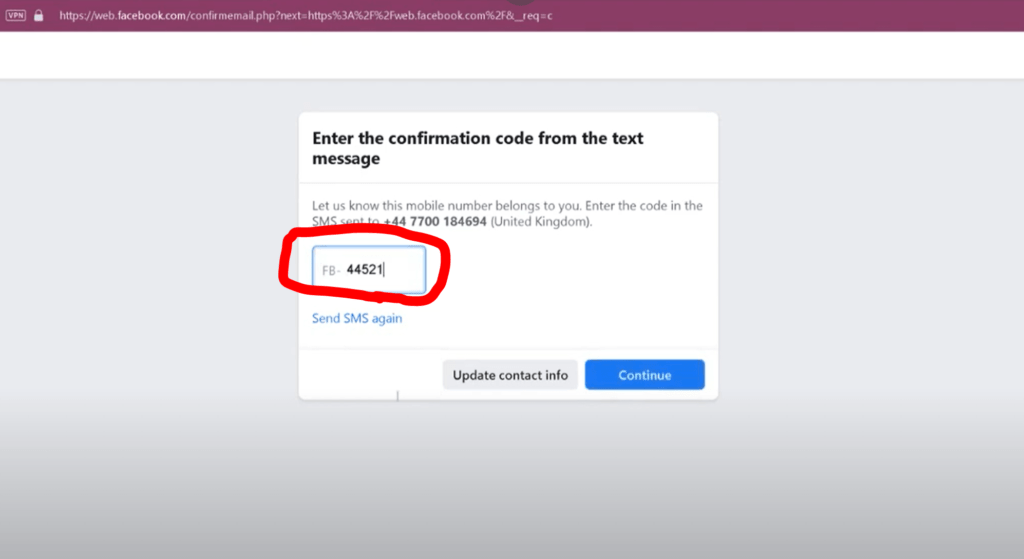
You can maintain your privacy while also ensuring the security of your online account by using our website’s Receive SMS service. We offer a safe and free way to obtain a temporary phone number for SMS or OTP verification.
Why Are Temp Numbers Used for SMS Verification?
The popularity of SMS verification has increased, but so have the difficulties that have resulted from it.
You have to have faith in the other party to give them your personal contact information if you allow SMS verification without using a phone.
There are numerous ways in which this could expose you.
Real SIM Numbers are a more expensive method of getting a temporary phone number than other options, but some people use them for SMS verification.
I believe that receiving SMS has a more powerful remedy for the issue.
What is the justification for businesses’ insistence on SMS Online verification?
These days, numerous companies are seriously concerned about information security breaches.
Data breaches could almost completely ruin a company’s reputation, because they are valuable.
So rather than taking the opportunity on cybersecurity incidents, the majority of organizations have added SMS verification as an extra measure of security.
SMS verification is indeed not one hundred percent trustable.
SMS verification is not always trustworthy. Just because a company uses SMS verification somehow doesn’t mean that data security risks are eliminated.
However, it does give businesses a legitimate argument in the event that critical data is exposed as a result of a data breach.
Skipping SMS verification is potentially possible?
Unfortunately, just about all entities will just not permit you to “opt out” of SMS validation.
Feel free to keep my mobile phone number in your address book, and I wish you the best of luck.
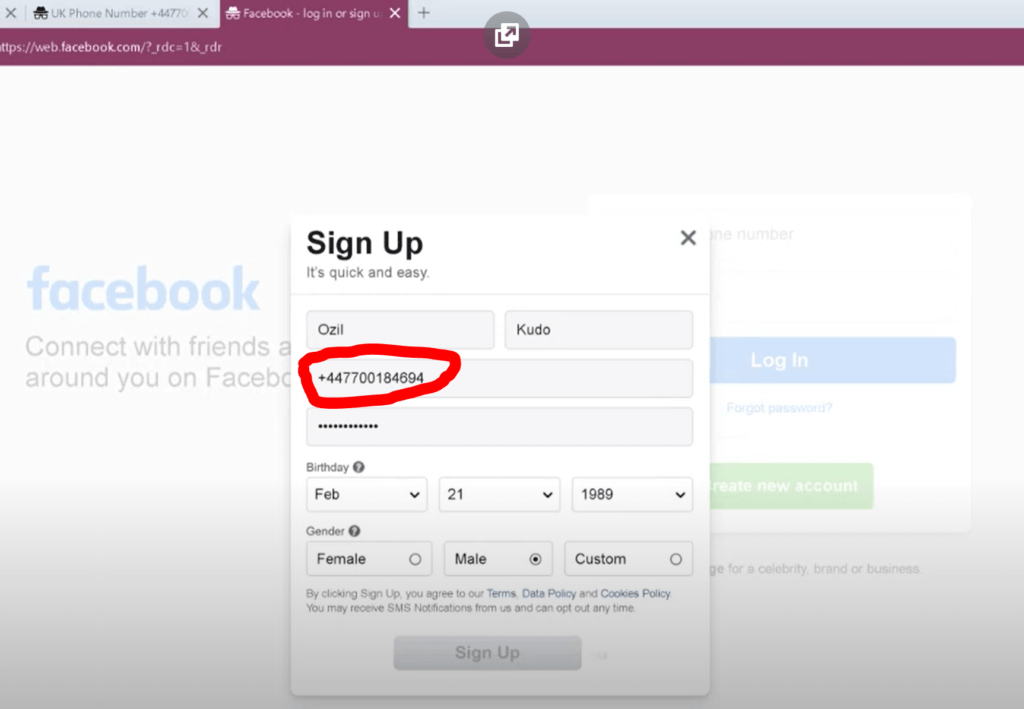
Receive SMS can provide users with such a secure, short lived mobile number to replace your current phone number.
Please, try not to involve your telephone for SMS confirmation.
Organizations might be satisfied with SMS verification, however it doesn’t suggest that their shoppers are as satisfied.
Coming up next are instances of techniques through which people can do this:
- Buying a burner telephone or an expendable telephone
- Utilizing a contraption claimed by a companion or relative
- Looking on the Internet for “temp phone numbers for SMS verification“
- Utilizing Google Voice to speak with others
Potential Problems With SMS Verification in temporary numbers
Several aspects could just go factually incorrect while using a service apart from receiving SMS to verify SMS messages.
An example might well be:
The utilization of sites on the internet providing free temporary phone numbers is expressly forbidden on some social networking sites, including Facebook.
You might not receive the code if you already have your phone’s do not disturb functionality activated or if you don’t have an internet connection.
Certain solutions might not send the verification code once they guarantee.
A few of those applications for fake mobile numbers are unsafe, but others might collect and sell your personally identifiable information. When using these apps, use caution.
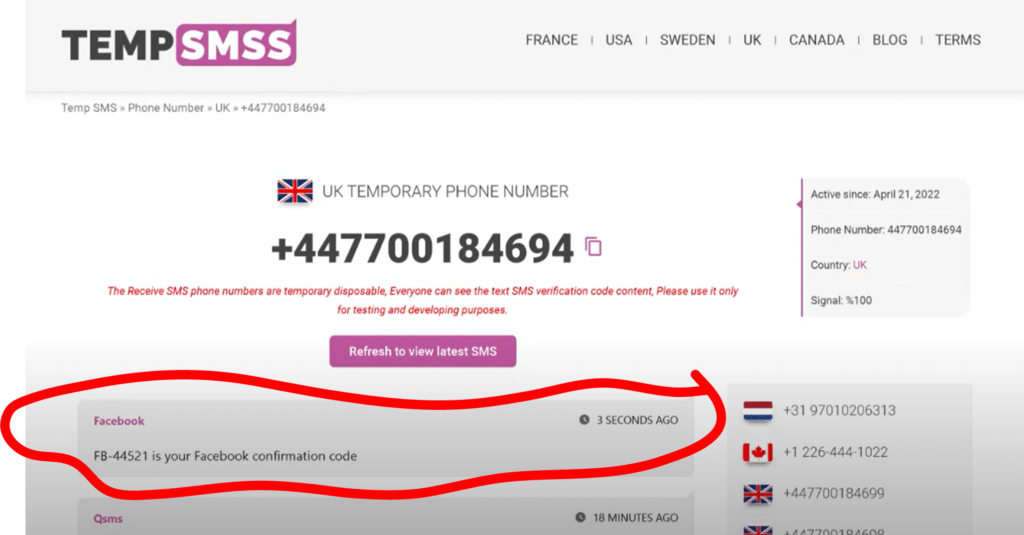
By using tempsmss.com, you’ll have the option to check SMS without having a telephone
With tempsmss.com, you’ll be able to get for digital services or indeed confirm SMS without the need for a mobile by using our temporary phone numbers opportunity.
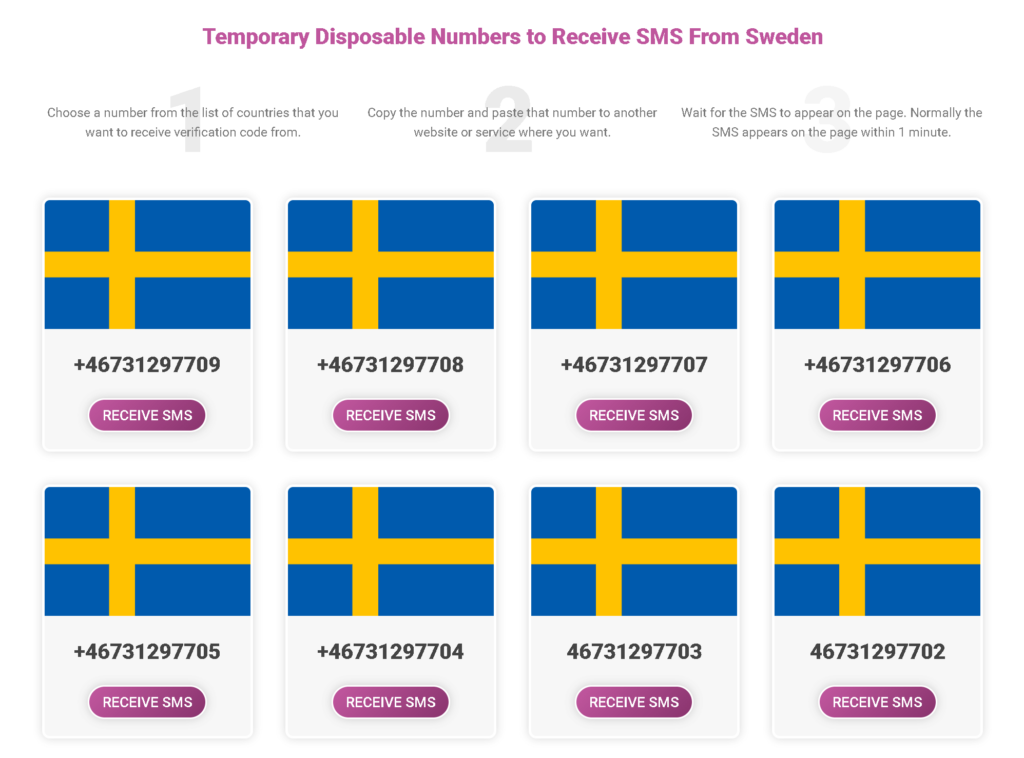
The steps listed below should be followed:
- To get a new SMS receiver number, explore the main website then click on a country.
- Choose the number from a country you wish to get SMS from.
- As soon as you need to, start using your new temporary phone number. The attributed mobile number is abruptly cancelled and the text message is deleted after a minute.
- From the drop-down menu, choose “receive a temporary SMS” as a result, received SMS will show up in the page and it can only be used once before being tried to replace.
What else is available in tempsmss.com, besides this?
A suitable technique of information exchange is text messaging, especially for fast and easy messages or dialogues that don’t call for the use of a phone.
However when you want to text someone and you don’t have your phone with you, the issue emerges.
You might also not even have a phone contract or dislike using a smartphone’s keyboard because it is too tiny for you.
In any case, it might even be useful to know how to receive text messages on a laptop.
Fortunately, you have access to some tools that will help you with just this project.
Discover more by having read on.
There are several options for receiving messages out of your device, regardless of whether you don’t have a prepaid sim card or need to do so.
By choosing a few of the aforementioned options, you can receive texts quickly and easily without a phone.